LIFESTYLE
Beware of New Android Trojan That Executes Malicious Commands
Cybersecurity researchers at XLab have uncovered a new Android malware strain called “Wpeeper.” This sophisticated backdoor Trojan has been designed to infiltrate Android systems and …
Read moreThreat Actors Attacking MS-SQL Servers to Deploy Ransomware
Cybersecurity experts have uncovered a series of sophisticated cyberattacks targeting poorly managed Microsoft SQL (MS-SQL) servers. The attackers, identified as the TargetCompany ransomware group, have …
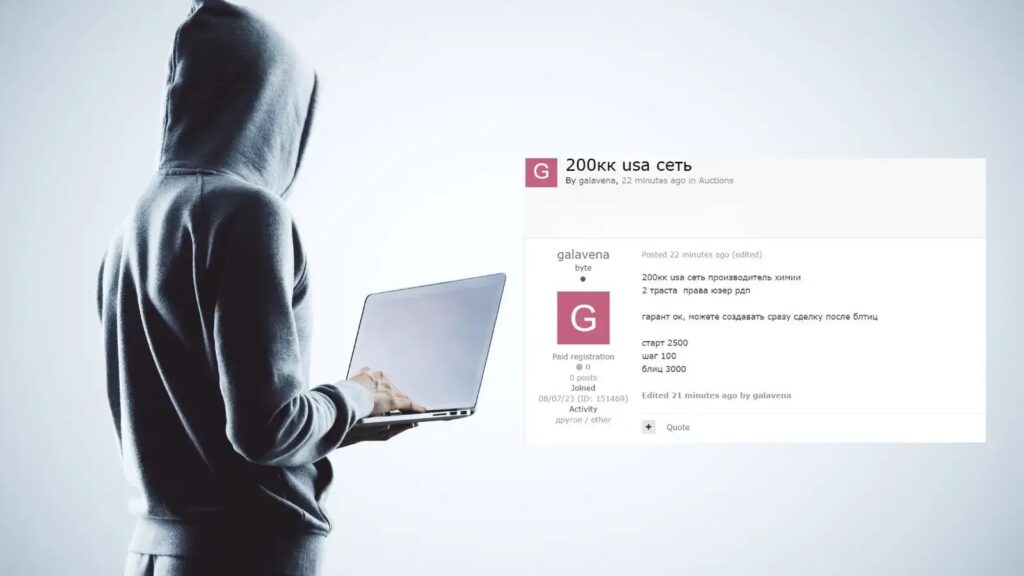
Read moreBeware! Threat Actors Selling RDP Access on Hacker Forums
Cybersecurity communities are on high alert as threat actors have begun selling Remote Desktop Protocol (RDP) access on underground hacker forums. This alarming trend poses …
Read moreEntertainment
Community

Beware of New Android Trojan That Executes Malicious Commands
Cybersecurity researchers at XLab have uncovered a new Android malware strain called “Wpeeper.” This sophisticated backdoor Trojan has been designed to infiltrate Android systems and …